1 million sites imperiled by dangerous bug in WordPress plugin
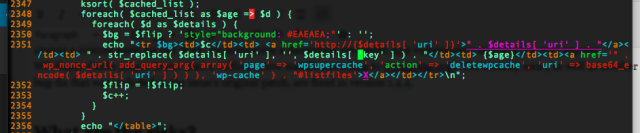
As many as a million websites could be imperiled by a critical vulnerability recently discovered in WP-Super-Cache, a WordPress plugin that generates static HTML files from dynamic WordPress blogs.
The persistent cross-site scripting bug allows attackers to insert malicious code into WordPress-published pages that use the extension, according to a blog post published Tuesday by security firm Sucuri. Anyone who relies on the plug in should immediately upgrade to version 1.4.4, which has fixes for that bug and several others.
Sucuri researcher Marc-Alexandre Montpas wrote:
Using this vulnerability, an attacker using a carefully crafted query could insert malicious scripts to the plugin’s cached file listing page. As this page requires a valid nonce in order to be displayed, a successful exploitation would require the site’s administrator to have a look at that particular section, manually.
When executed, the injected scripts could be used to perform a lot of other things like adding a new administrator account to the site, injecting backdoors by using WordPress theme edition tools, etc.
The bug lies in the way WP-Super-Cache displays information stored in the cache file key. In vulnerable versions, user-supplied data was appended to the page contents without being scrubbed clean of any potentially malicious commands.